Overpower Threats.
Empower IT.
Powerfully simple endpoint security that takes down threats, without interrupting business.
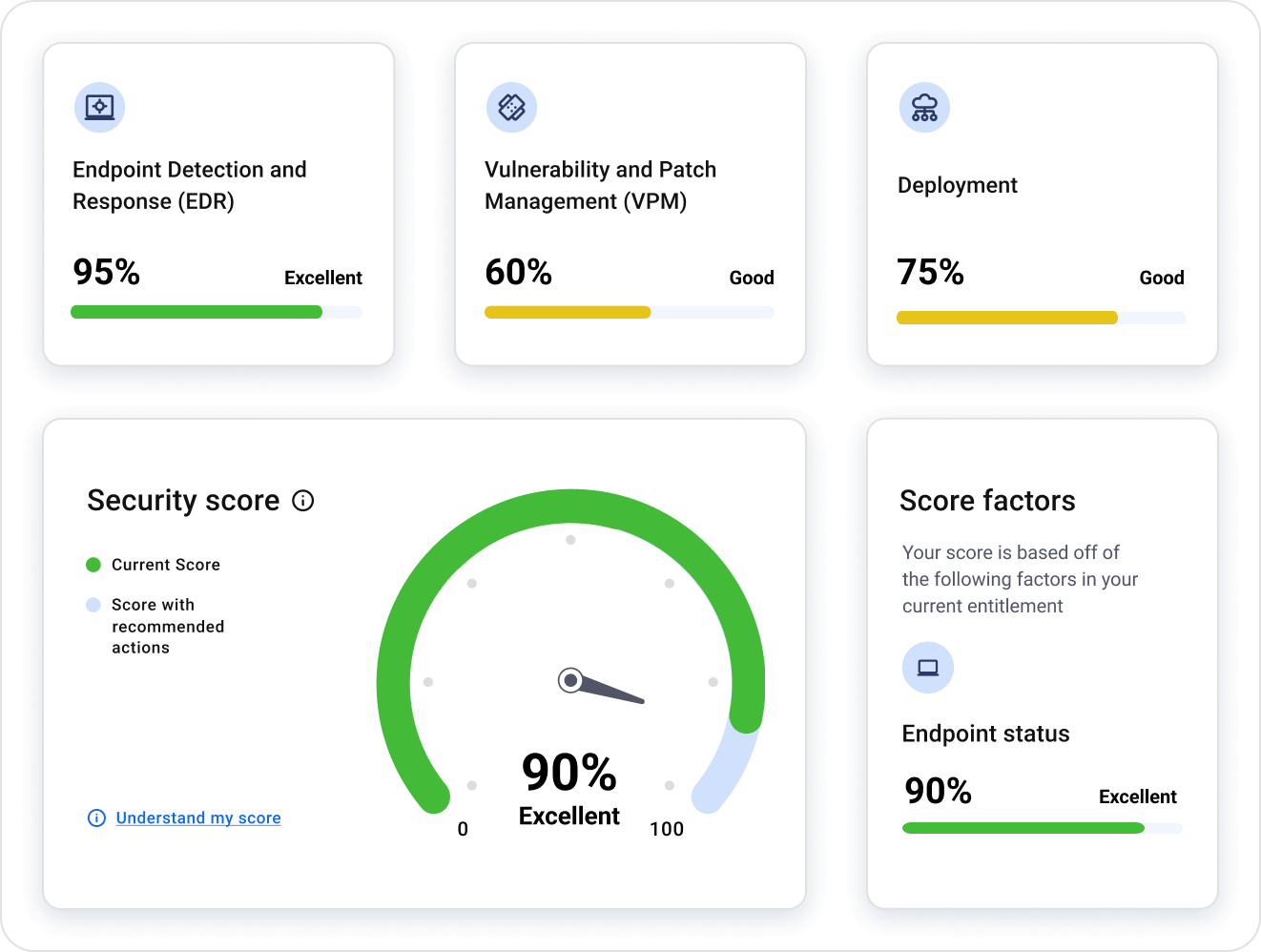
Carbon Black leaving you in the dark?
Bring your
threat level
down
OUR SOLUTIONS
We get it – security is hard.
Security products shouldn’t be.
Core
Next-gen AV and threat surface reduction.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
Optional add-ons:
-
Core for Servers /
-
Mobile Security / $10
Advanced
Everything in Core plus expanded threat surface protection.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Threat Hunting
Optional add-ons:
-
Advanced for Servers /
-
Mobile Security / $10
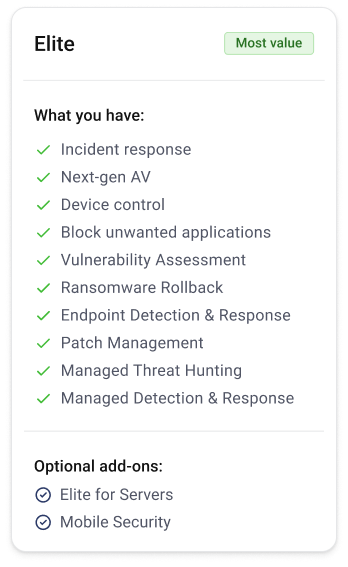
Elite
Everything in Advanced plus fully managed detection and response.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
Optional add-ons:
-
Elite for Servers /
-
Mobile Security / $10
Ultimate
Everything in Elite plus protection against malicious websites.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
-
DNS (Web Content) Filtering
Optional add-ons:
-
Ultimate for Servers /
-
Mobile Security / $10
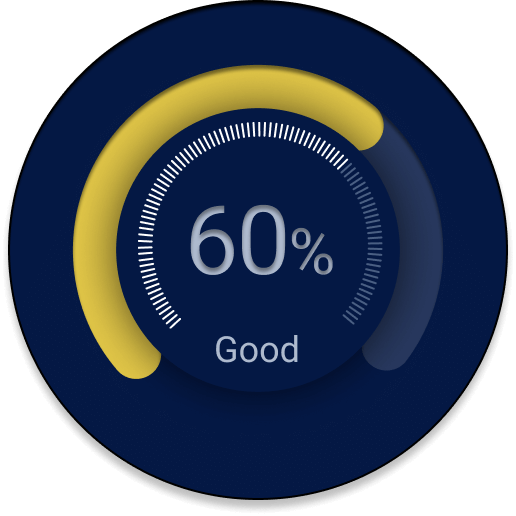
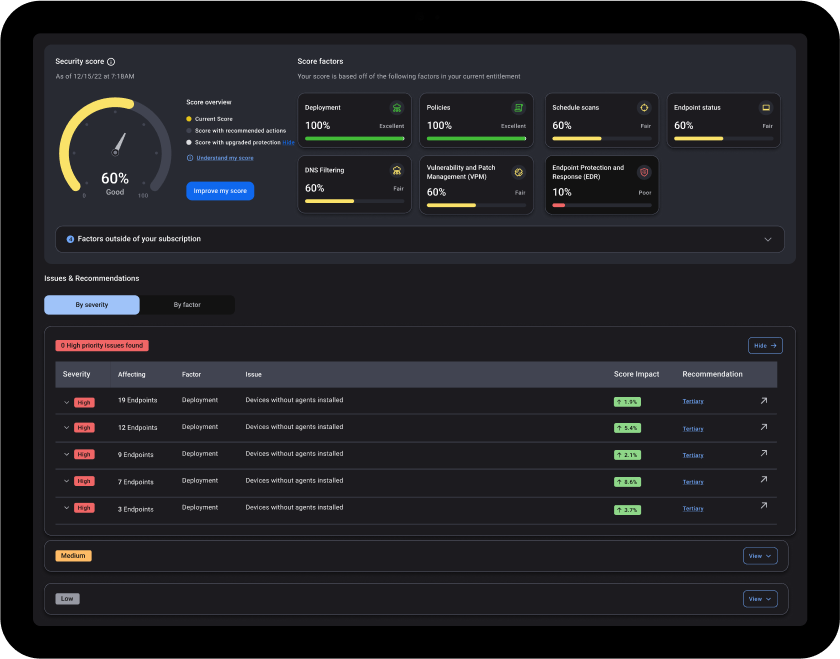
Bring your threat levels down with Security Advisor
Visualize and optimize your security posture in just minutes.
- At-a-glance security score
- Issue prioritization
- Instant advice & action
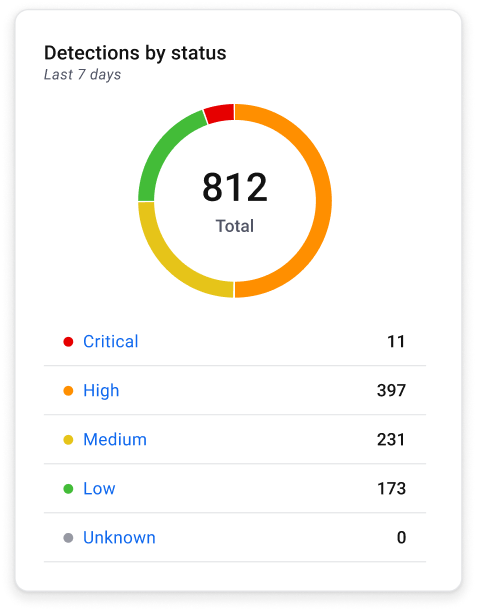
Industry Accolades and Peer Reviews
3rd Party Test Results
ThreatDown solutions are consistently top-rated amongst analysts, customers and independent third parties.
| 360 Assessment Level 1 Certified |
Exploit Certified |
Online Banking Certified |
Ransomware Certified |
|
|---|---|---|---|---|
| Malwarebytes | ||||
| Symantec | X | |||
| Bitdefender | X | |||
| Microsoft | X | X | X | |
| Avast | X | X | ||
| ESET | X | |||
| Avira | X | X | X | |
| Trend Micro | X | X | X |
Take Threats Down
Award-winning endpoint security solutions that combine layers of protection, threat intelligence, and human expertise to protect organizations from ransomware, malware, viruses and other threats.
Take Complexity Down
ThreatDown solutions provide complete, integrated protection through one single, lightweight agent. Our solutions are incredibly fast to install and easy to manage.
Take Costs Down
ThreatDown solutions are built for everyone- not just companies with deep pockets and large security teams. Our solutions combine technology with services to provide robust protection that’s efficient and cost-effective.
15k+
Business, schools, governments and more
9.2M+
Monthly remediations
3M+
Endpoints protected
ThreatDown, born from Malwarebytes
Built on our decade plus of experience with malware detection and remediation, ThreatDown offers best-in-class endpoint security solutions designed to protect organizations just like yours.



